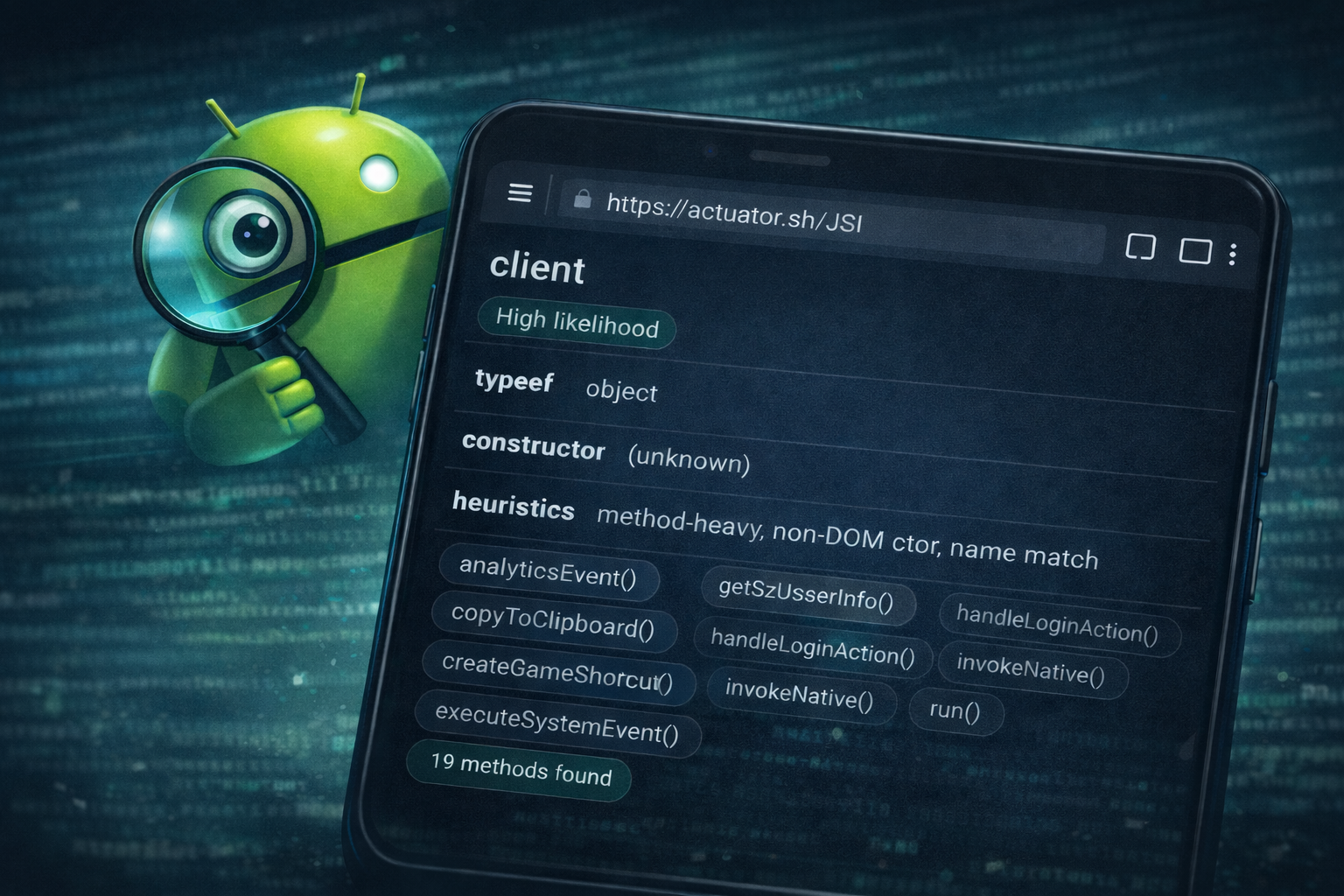
WebView remains one of the most frequently misunderstood integration surfaces in Android applications.
The addJavascriptInterface mechanism enables powerful hybrid functionality, but when improperly scoped,
can expose privileged application behavior to untrusted content.
In most cases, exposed interfaces are not introduced deliberately. They commonly originate from legacy debugging hooks, temporary instrumentation, or developer convenience methods that persist into production builds. These conditions are rarely obvious during static review and are often only observable when examining runtime behavior.
This distinction matters. The difference between assumed exposure and actual exposure at runtime frequently defines whether a risk is theoretical or practically exploitable.
The JSI Scanner is a lightweight utility intended to support this analysis. It enumerates JavaScript interfaces exposed to WebView at runtime and presents them in a form suitable for manual inspection during assessment.